We briefly covered voice access ports earlier in the chapter also mentioning voice VLANs. It is time now to dig a bit deeper into voice VLANs and do a little configuration as well.
The voice VLAN is an ingenious feature that enables access ports to carry voice traffic from an IP phone. Cisco IP phones connect to the IP network using Ethernet to send Voice over IP (VoIP) packets. The Voice over IP framework is made up of several components including IP phones, call managers, and voice gateways. A detailed coverage of these components is beyond the scope of this book and your Cisco Certified Network Associate (CCNA) exam. The VoIP communication takes place over the same shared network infrastructure made up of switches and routers which is used for data communication.
Each desk or cubicle in a modern enterprise is likely to have both an IP phone and a PC on it. One way of connecting the IP phone to switch may have been to use a separate Ethernet cable and a separate switch port. But Cisco came up with the idea of including a small LAN switch built inside each Cisco IP phone. This small switch allows one cable to run from the LAN switch to the desk to connect to the switch built into the IP phone. Then the PC can connect to the switch inside the IP phone over a short straight-through Ethernet cable from the PC to the bottom of the IP phone. If you have access to a Cisco IP Phone, turn it upside down and you would find two Ethernet ports at its bottom. One port is to be connected to the LAN switch, the second port is to be connected to the PC and the third port is internal which connects to the IP phone circuitry inside. This is the simple three port switch built into all Cisco IP phones. In this way, a Cisco IP phone provides a data connection for a user’s PC, in addition to its own voice data stream. Please see figure below for a graphical representation of the concept just described.
Figure 7-14 Built-in Switch of the Cisco IP Phone
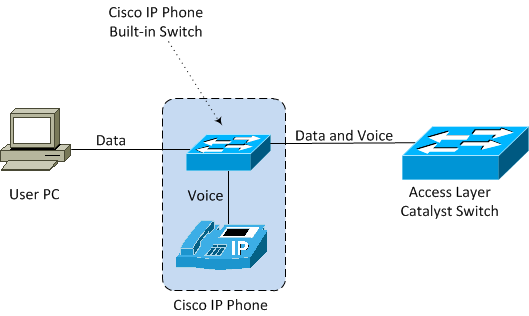
As you can see in the diagram, the link between the phone and switch should use 802.1Q trunking, and the phone and PC should be in different VLANs and hence in different IP subnets. This design is per Cisco recommended guidelines and has several advantages. First, by placing IP phones in one VLAN, and the PCs connected to phones in a different VLAN, you can more easily manage the IP address space, apply Quality of Service (QoS), and provide better security by isolating the data and voice traffic.
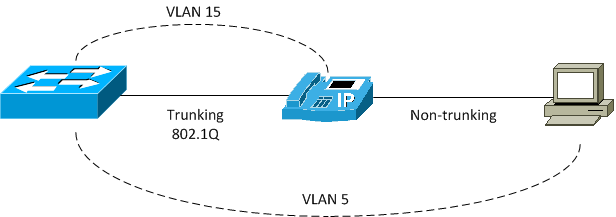
Figure 7-15 How to Connect an IP Phone and PC to LAN Switch
On a relatively quiet, underutilized network, a switch can generally forward frames as soon as they are received. However, if a network is congested, packets cannot always be delivered in a timely manner. Different types of applications have different requirements for how their data should be sent end to end. For example, it might be acceptable to wait a short time for a Web page to be displayed after a user has requested it. Also, an FTP download may continue at a variable rate without issues as user can use the file once it is fully downloaded. But it is probably not tolerable to face the same delays in receiving packets that belong to a streaming video presentation or a telephone call. Video streaming is very popular these days and typically multicast traffic over UDP as the transport protocol is used to transmit the video stream from a server to several clients. Any loss or delay in packet delivery would ruin the purpose of these applications due to their real-time or interactive nature.
Traditionally network congestion has been handled by increasing link bandwidths and enhancing switching hardware performance. This approach is not cost effective or efficient and it does nothing to address how one type of traffic can be preferred over another. Quality of Service (QoS) can be used to protect and prioritize time-critical traffic like voice and video. Keep in mind that the most important aspect of transporting voice traffic across a switched network is maintaining the proper Quality of Service level. Voice packets must be delivered in the most timely manner possible, with minimum jitter, loss, and delay.
As a matter of fact, layer 2 frames have no means to indicate the priority or importance of their contents for the purpose of prioritization or QoS. One frame looks just as important as any other frame. However, when frames are carried from switch to switch, an opportunity for classification occurs. We understand that a trunk is used to carry frames from multiple VLANs between switches. The trunk does this by encapsulating the frames and adding a tag indicating the source VLAN number. The encapsulation also includes a field that can mark the class of service (CoS) of each frame. This marking can be used at switch boundaries to make QoS decision and prioritize traffic according to importance. Cisco switches typically perform QoS implementation or traffic prioritization in hardware and the actual mechanisms may vary from platform to platform.
The LAN used for voice traffic from the IP phone is called the voice VLAN and the VLAN used for data is called the data or access VLAN. For the LAN switch to forward traffic correctly, it needs to know the VLAN ID of the voice VLAN as well as the data VLAN. The data or access VLAN is configured just as a regular access VLAN is configured using the switchport access vlan vlan-id command. The voice VLAN is configured using the switchport voice vlan vlan-id interface configuration mode command. Referring to the diagram, the switch would need both the switchport access vlan 5 and switchport voice vlan 15 commands in interface configuration mode.
SW1(config)#interface Fa0/1
SW1(config-if)#switchport access vlan 5
SW1(config-if)#switchport voice vlan 15
Summary
This chapter introduced to you a number of enhanced switching technologies and described how you can configure them on Cisco switches. We started with talking about virtual LANs (VLANs) and how they break up broadcast domains in a switched network and provide traffic isolation at layer 2. This fact is very important because layer 2 switches without VLANs only break up collision domains and your switched network is one large broadcast domain. We learned what access links are and also went over how trunked VLANs work across a Fast Ethernet of Gigabit Ethernet link.
Trunking is an important and critical technology to understand as most of the enhanced switching technologies described in this chapter invlove trunking one way or the other. We went into great detail describing VLAN Trunking Protocol (VTP) and learned how it sends VLAN information to all switches in the network over trunked links. We also leaernt how to configure and troubleshoot VTP in case things don’t work as you expect them to work.
Finally we covered Voice VLANs which can be used to allow IP phones to run along with regular desktop or laptop computers over your access switch ports. We finished off the chapter with detailed configuration and troubleshooting examples for almost all technologies covered in the chapter.Questions
Read the questions carefully and try to answer as many questions correctly as you can. Answers to these questions are provided on the next page.
1. Based on the exhibit shown for the local area network of an office comprising two departments, which of the following are correct ? (Choose two)
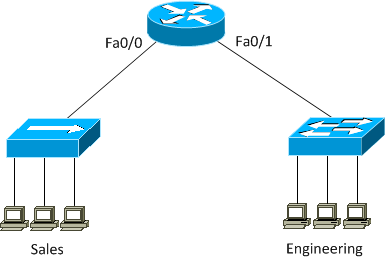
A. There are six collision domains in the network
B. There are two broadcast domains in the network
C. There are four broadcast domains in the network
D. There are six broadcast domains in the network
E. There are five collision domains in the network
2. An Ethernet switch receives a unicast frame with a destination MAC address that is listed in the MAC address table. What will the switch do with the frame?
A. The switch will forward the frame to a specific port
B. The switch will forward the frame to all ports except the port on which it was received
C. The switch will send a copy of the frame out the same port on which it was received
D. The switch will not forward the frame at all
E. The switch will add the destination MAC address in the frame to the MAC address table
F. None of the above
3. A switch port is configured as a VLAN trunk. Which of the following trunk modes are valid ? (Select all that apply.)
A. Blocking
B. Dynamic auto
C. Dynamic desirable
D. On
E. Transparent
F. All of the above
4. Which of the following frame encapsulation methods can be configured on Cisco switch trunks? (Select two.)
A. 802.1Q
B. VTP
C. CDP
D. Auto
E. Desirable
F. ISL
5. You need to configure two switches to exchange VLAN information. Which protocol provides the functionality of sharing VLAN information between these two switches?
A. STP
B. RSTP
C. 802.1Q
D. ISL
E. VTP
F. None of the above
Q6. Which of the following statements are true regarding how VLANs are used to segment a network? (Select three)
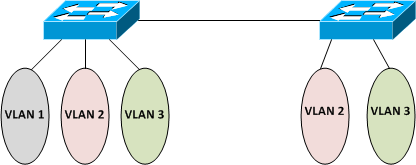
A. VLANs increase the size of collision domains.
B. VLANs increase the size of broadcast domain while decreasing the number of collision domains.
C. VLANs increase the number of broadcast domains while decreasing their size.
D. VLANs allow logical grouping of users by function.
E. VLANs can enhance network security.
F. VLANs simplify switch administration.
7. Two switches have been configured with static VLANs as shown in the figure. But VLAN 2 on switch A has no connectivity with VLAN 3 on switch B. How should the network administrator solve the problem?
A. Configure interconnected ports on switch A and switch B in access mode.
B. Connect the two switches using a straight-through cable.
C. Configure VLAN 1 with IP addresses on both switches.
D. Add a layer 3 device to provide connectivity between VLAN 2 and VLAN 3.
D. Ensure that VTP passwords match on both switches.
8. Which of the following steps are basic requirements in order to add a new VLAN to a switched network?
A. Create the VLAN.
B. Name the VLAN.
C. Configure an IP address for the VLAN.
D. Add the desired switch ports to the new VLAN.
E. Add the VLAN to the VTP domain.
9. You connect a new PC to a free port on a switch, but you find that the PC cannot access any of the resources on the LAN. No other PC connected to the switch has connectivity issues. What is the most likely cause of this problem?
A. The MAC address is not configured correctly on the host.
B. An STP instance is not running for the new host.
C. The switch does not have the MAC address of the new host hard coded in the MAC address table.
D. The switch port host is connected to is assigned to the incorrect VLAN.
E. The router has not learned the route to the new host.
10. Please study the exhibit carefully. The switch has twenty four Fast Ethernet ports and two Gigabit Ethernet ports. But why are some ports missing from the list of ports assigned to the default VLAN?
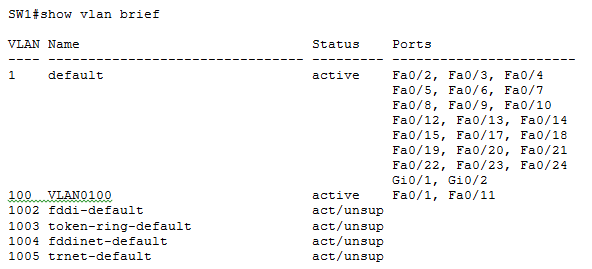
A. The missing ports are administratively shut down.
B. The missing ports are not actively participating in STP
C. The missing ports are assigned to VLAN 100.
D. The missing ports are configured as trunk ports.
E. The missing ports have a speed or duplex mismatch with neighboring ports.
F. None of the above.
Answers
1. B, E
2. A
3. B, C, D
4. A, F
5. E
6. C, D, E
7. C
8. A, D
9. D
10. C
