With static NAT, a particular inside local address always maps to a particular inside global (public) address. Due to one-to-one mapping between addresses static NAT does not conserve public IP addresses. Although static NAT does not help with IP address conservation, it provides a degree of security by hiding the inside IP addresses from the outside world. Static NAT also allows an administrator to make an inside server available to clients on the Internet, because the inside server will always use the same public IP addresses.

Let’s configure router R1 performing NAT as depicted in Figure 10-3.
Figure 10-3 NAT Scenario
Here is how the configuration goes.
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip nat source static 192.168.1.2 67.210.97.2
R1(config)#ip nat source static 192.168.1.3 67.210.97.3
R1(config)#ip nat source static 192.168.1.4 67.210.97.4
R1(config)#interface FastEthernet0/0
R1(config-if)#ip address 192.168.1.1 255.255.255.0
R1(config-if)#ip nat inside
R1(config-if)#interface FastEthernet0/1
R1(config-if)#ip address 67.210.97.212 255.255.255.0
R1(config-if)#ip nat outside
R1(config-if)#end
R1#
The ip nat inside source command identifies which IP addresses will be translated. In the preceding configuration example, the ip nat inside source command configures a static translation between inside local and inside global IP addresses as shown in Table 10-2 below.
Table 10-3 Static NAT Address Mapping
| Inside Local Addresses | Inside Global Addresses |
| 192.168.1.2 | 67.210.97.2 |
| 192.168.1.3 | 67.210.97.3 |
| 192.168.1.4 | 67.210.97.4 |
You may also identify an ip nat command under each interface in the above configuration. The ip nat inside command identifies an interface as the inside interface. The ip nat outside command identifies an interface as the outside interface. The ip nat inside source command is actually referencing the inside interface with the inside keyword and the source address with the source keyword. The static keyword indicates a static one-to-one mapping between inside local and inside global addresses.

The ip nat inside source command is simply instructing the router to translate the source address of every packet entering the router at the inside interface. In order to ensure two-way communication return packets coming in the outside interfaces are also translated accordingly.
Once you finish your NAT configuration, you would usually want to verify if the configuration is working as expected or not. Also, you may need to monitor NAT translations in a production environment. It is quite tempting to use show running-config command to verify that the NAT configuration lines you entered are actually there in the running configuration of the router. But this does not tell you anything about whether actual translation of addresses is taking place or not.
The starting point for NAT verification and troubleshooting should be the show ip nat translations command:
Pro Inside global Inside local Outside local Outside global
— 67.210.91.2 192.168.1.2 — —
— 67.210.91.3 192.168.1.3 — —
— 67.210.91.4 192.168.1.4 — —
The output above shows inside local addresses mapped to inside global address as configured on R1 and summarized in Table 10-2. What’s shown in the above output does not include any real translations so far because inside hosts did not send any traffic yet. What we see so far is the result of the three ip nat inside source commands in our configuration. In order to see some real translations we would generate some traffic by pinging the server 173.194.67.102 from each of the three inside hosts and run the show ip nat translations command again on R1:
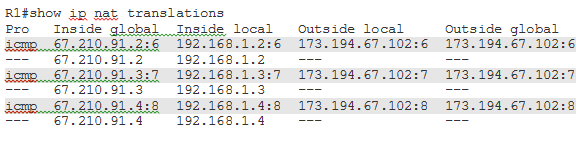
In the above output, you can see three dynamic entries show in gray, each corresponding to a ping from an inside host to the server 173.194.67.102. Typically you would see several dynamic entries in the translation table for the same inside host communicating with several outside hosts using various protocols.
Another useful tool for NAT verification is the show ip nat statistics command:
Total active translations: 3 (3 static, 0 dynamic; 0 extended)
Outside interfaces:
Serial1/0
Inside interfaces:
FastEthernet0/0
Hits: 27 Misses: 3
CEF Translated packets: 30, CEF Punted packets: 0
Expired translations: 3
Dynamic mappings:
Queued Packets: 0
This command provides NAT statistics including the number of translated packets or hits.
Please note that translation table entries eventually time out. However you may also use the clear ip nat translations command to clear specific entries from the translation table before they time out on their own. In order to clear all entries from the translation table, use an asterisk (*) at the end of the command:
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
— 67.210.91.2 192.168.1.2 — —
— 67.210.91.3 192.168.1.3 — —
— 67.210.91.4 192.168.1.4 — —
As you can see in the above output, the ICMP translation entries are all gone following the clear ip nat translations * command.
