Standard access lists are the oldest type of access lists, dating back as early as Cisco IOS Software Release 8.3. Standard access lists control traffic by comparing the source address of packets to the addresses configured in the access list.
In all software releases, the access list number for the standard IP access lists can be anything from 1 to 99. In Cisco IOS Software Release 12.0.1, standard IP access lists began using additional numbers from 1300 to 1999. These additional numbers are sometimes referred to as the expanded range. In addition to using numbers to identify access lists, Cisco IOS Software Release 11.2 and later added the ability to use names to define standard IP access lists. We will learn how to configure both numbered and named access lists as we proceed in this chapter.
Table 9-6 Access List Types and Corresponding Numbers
| Access List Type | Number Range |
| IP Standard Access Lists | 1-99 |
| IP Standard Access Lists (expanded range) | 1300-1999 |
| IP Extended Access Lists | 100-199 |
| IP Extended Access Lists (expanded range) | 2000-2699 |
You can differentiate between standard and extended access lists in the numbered format simply by looking at the access list number. Based on the number used when access list is created, the router also knows which type of syntax to expect as the list is entered. By using numbers 1 – 99 or 1300 – 1999, you are essentially telling the router that you want to create a standard IP access list. Thus the router will expect the standard IP access list syntax specifying only the source IP address in access list entries.
Creating a Numbered Standard Access List
If you want to filter traffic using source IP address only, a standard access list is a simple and sufficient option. Probably the best way to show you how to configure a numbered standard access list is by showing you how to do it one step at a time:
<1-99> IP standard access list
<100-199> IP extended access list
<1100-1199> Extended 48-bit MAC address access list
<1300-1999> IP standard access list (expanded range)
<200-299> Protocol type-code access list
<2000-2699> IP extended access list (expanded range)
<700-799> 48-bit MAC address access list
dynamic-extended Extend the dynamic ACL absolute timer
rate-limit Simple rate-limit specific access list
The command to create an access list, not surprisingly, is access-list entered in configuration mode. As we just discussed the number we use to identify an access list cannot be any arbitrary number. This number rather must belong to the range of numbers available for the type of access list you want to create. At the moment, we are interested in creating a standard numbered access list. So we can choose a number from the ranges 1-99 or 1300-1999.
deny Specify packets to reject
permit Specify packets to forward
remark Access list entry comment
We chose to use 1 as our standard access list number and there are three keywords available now as you can see from above output. Let’s first add a user-friendly remark in order to make our access list more readable as we return to it at a later point in time. A remark of upto 100 characters can precede or follow an access control entry. We will add a remark before the entry though you can choose to add remarks following access list entries. You should be consistent throughout your configuration whether you choose to add remarks before or after access control entries.
As you may have guessed from the remark, we are going to create an access control entry that would allow all traffic sourced from Bob’s IP address 172.16.23.3. We use the wildcard mask 0.0.0.0 in order to match all bits in the source IP address. If the source wildcard mask is omitted, a wildcard mask of 0.0.0.0 is assumed. So, in this case we may even have omitted the wildcard mask of 0.0.0.0 but it is good practice to always explicitly mention the wildcard mask to make configuration readily understandable. Keep in mind that good configuration is one that is easy to read and understand, not one that is cryptic and unnecessarily complex.
Exactly the same result can be achieved using the host keyword.
We can use either of the two formats just described to have exactly the same effect. Let’s move on to create our next access control entry denying access to Max.
Now that’s interesting as we intend to not only deny access to Max but also to log any access attempts made by him using the log keyword at the end of the statement.
At this point, the access list has actually been created and the same can be verified. This access list would be visible in the running configuration of the router when you use the command show running-config using the include keyword to filter output showing only those lines in the running configuration that contain the access-list keyword.
access-list 1 permit 172.16.23.0 0.0.0.255
access-list 1 remark Block all traffic from network 172.16.23.0/24
Another useful command to verify access lists is show access-lists:
Standard IP access list 1
10 permit 172.16.23.0, wildcard bits 0.0.0.255
Though the access list has been created now but it is sitting idle, doing nothing as it has actually not been applied to any interface. Let’s go ahead and apply it to interface Fa0/0 in the inbound direction as depicted in Figure 9-2.
Figure 9-2 Standard Numbered Access List Example
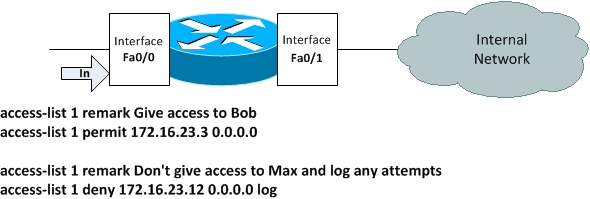
The command to apply an access list to an interface is ip access-group entered in interface configuration mode:
R1(config)#int Fa0/0
R1(config-if)#ip access-group 1 ?
in inbound packets
out outbound packets
R1(config-if)#ip access-group 1 in
R1(config-if)#
As you can see, there are two options available while applying an access list to an interface, those are, in and out. We have applied the access list in the inbound direction filtering packets coming into the interface from outside. The access list is now applied comparing all packets received on interface Fa0/0 against entries in access list 1 and taking appropriate action.
Let’s run a final check verifying if the access list has been successfuly applied to the router interface:
FastEthernet0/0 is up, line protocol is up
Internet address is 192.168.1.1/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 1
<Output omitted for brevity>
R1#
Creating a Named Standard Access List
A standard named access list can be used if you need to filter on source address only. Ther is no difference between numbered and named access lists in terms of functionality, however each has its own syntax. We will define a standard named access list including one permit statement and one deny statement. The actual statements you use and their order would depend on your filtering requirements. You should define your permit and deny statments depending on what you want to allow or block.
Enter privileged exec mode using enable command, and move to the golbal configuration mode using configure terminal command. You can configure access lists from the global configuration mode just like any other configuration on Cisco devices.
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
The command used to define a named access list is ip access-list which has several options:
extended Extended Access List
log-update Control access list log updates
logging Control access list logging
resequence Resequence Access List
standard Standard Access List
We are specifically interested here in two of these options: standard and extended, used respectively to defined standard and extended access lists. We will proceed to define and standard access list named Corp.
Let’s now define access list statements preceded by remarks to make their meaning clear. The first access list entry denies the whole class B network 172.18.0.0 belonging to the Operations department and also logs any unsuccessful attempts using the log keyword.
R1(config-std-nacl)#deny 172.18.0.0 0.0.255.255 log
But the CEO has an IP address 172.16.3.24 and he still needs to have access, so we create a permit statement to do just the same.
R1(config-std-nacl)#permit 172.16.3.24 0.0.0.0
R1(config-std-nacl)#end
And that’s all! The access list has been created which can be verified using command show ip access-list.
Standard IP access list Corp
20 permit 172.18.3.24
10 deny 172.18.0.0, wildcard bits 0.0.255.255 log

And let’s have a look at the figure before applying the access list to an interface.
Figure 9-3 Standard, Named Access List Example
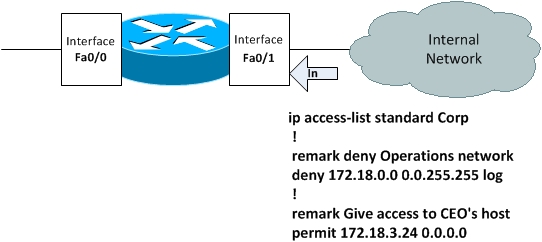
Let’s now finalize out configuration by applying the access list to router interface Fa0/1 in the inbound direction.
R1(config-if)#ip access-group Corp in
You can now verify if access list has actually been applied to the interface Fa0/1 using command show ip interface.
FastEthernet0/1 is up, line protocol is up
Internet address is 192.168.1.1/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is Corp
<Output omitted for brevity>
R1#
